Friday, March 5, 2010
Exploiting Google
No, it's not another buzz word. It's a technique used by malware authors to propagate their malware. They use one of the most respected search engines today (Google) to make their way into the user's machine. Piggybacking on a prestigious, and highly trusted search engine is an efficient and effective way to reach out to billions of users worldwide.
Rogue AVs usually use this method. They create fraudulent sites (site A) which redirects to another site (site B) which in turn downloads Rogue AVs into the system. The malware industry makes sure that Site A gets a hit during Google search by targeting search queries that are sensational or new, for example, the Haiti earthquake.
In light of this, users are advised to be vigilant when accessing sites. When even Google is used as a medium by malwares, blind trust on returned links is unacceptable.
Virus.Virut takes the spotlight
Last year we saw an influx of Virus.Virut infected samples. Virus.Virut is, in my opinion, one of the best viruses in a while. Despite the fact that viruses are harmful, I cannot help but admire the work done to create such a virus.
Virut is a polymorphic file infector. What makes Virut different is the fact that it employs all known infection routines: Entry-Point Obscuring, appending, prepending, cavity. Not only does it employ all these techniques, it can combine them (e.g. EPO appending, EPO + cavity + appending, cavity + appending). It also has decryption layers, the algorithm of which can change from ADD/ SUB/ XOR, etc. Both detection and analysis pose as a challenge, but is one that the antimalware industry has met head-on.
xoxo
Disasterware strikes again, as they call it!
Once unsuspecting users click the malicious site, it will be redirected to fake AV online scan page and shows different annoying pop-ups warning the user that his system is infected and vulnerable to attacks. This might lead the user to download and install the Rogue Antispyware such as Security Antivirus. They have used multiple malicious domain names to prevent them to be easily identified. This infection routine is the same with other reports as you might have read from the previous blogs. But despite of awareness campaign, there are still an increasing number of victims fallen to this scam and worst, lost their money.
I have seen few malicious searched results which start with comma (,) and dash (-) such as above screen shot and from this blog. It is advisable to prevent from visiting these kinds of searched results. Internet users should be very careful in picking which sites to read the latest news. It is much better to read from reputable sources.
Monday, March 1, 2010
Chilling rogues on Chile
Searches returned from google are generally not suspect, especially if they bear URLs that seem normal. But one particular site (bostonmassduilawyer.com/ypi.php?...chile-earthquake-videos) when accessed will redirect you to http://188.124.5.159/index.html.

This site will display a fake system scan using an HTML page, and clicking anywhere on the page will prompt the user to download the INST.EXE file (SecurityTool fake AV). It also displays annoying popups that feeds FUD to users (FUD: Fear, Uncertainty, Doubt).


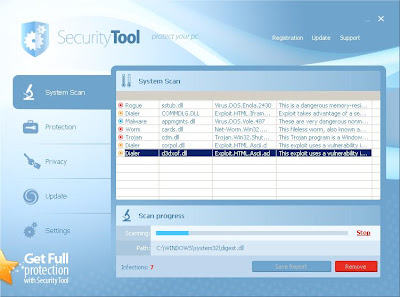
INST.EXE is just another Security Tool installer. Shortly after executing, it will display a fake scan showing some bogus results. Attempting to activate it will lead you to a page where they offer you a 2 year software license of $49.95, and a lifetime software license of $79.95. Looks tempting, but it's just a ploy to part you with your money. In truth, it's one hell of a hefty price to pay for such a useless and annoying scareware.




Wednesday, February 24, 2010
How To Remove: Security Essentials 2010
 Security Essentials 2010 (SE2010.exe) is a new rogue application which is usually arrives as a file dropped by a Trojan or downloaded from the internet. It employs the same techniques as of Internet Security 2010…then again, said techniques have proven effective before, so why fix what is not broken?
Security Essentials 2010 (SE2010.exe) is a new rogue application which is usually arrives as a file dropped by a Trojan or downloaded from the internet. It employs the same techniques as of Internet Security 2010…then again, said techniques have proven effective before, so why fix what is not broken?Without being asked, SE2010 scans the infected computer and displays the list of threats present in the system. Note that the said list is fake and the files do not really exist.
Tuesday, February 23, 2010
SEO Poisoning scores a goal at the 2010 Winter Olympics
Countermeasure Against the Good Guys
Malware researchers often share URLs with each other as a way of spreading the news and to warn others and prevent further infection. But the bad guys behind this attack are smart enough to devise a countermeasure. The URLs are no longer enough to replicate the attack. Entering the URL directly on the browser simply redirects the users to the CNN website.
As mentioned in a previous post, Security Antivirus is a clone of Live PC Care, Windows Security Suite, and Windows System Suite.
Monday, February 22, 2010
Rogues on Winter Olympics' Playing Field
Search result for luger’s death. Clicking the search result (in red box) would redirect to RogueAV
Internet users who wanted to be updated with this news will unknowingly visit one of these malicious sites. Redirections will occur until the user will experience fake AV pop-ups and enticing them to download the malicious installer file..
WINTER OLYMPIC’S MEDAL STANDING
Another Malware Writers takes advantage of as the winter Olympics are on-going is the medal standings of each participating countries. They use keyword such as “Medal Count”, “Olympic medal count”, “Olympic standing” in order to be included in search engines and be able to infect users.
Search result for Winter Olympic Medal Standings. Clicking the search result (in red box) would redirect to RogueAV.
Unaware users who wanted to look for medal standings will unknowingly visit one of these malicious sites. Visiting these malicious URLS will download Rogue AV and make the user’s computer have annoying pop ups.
REDIRECTIONS
Upon clicking the enticing malicious URL / link, there will be redirections and some different enticing pop-up messages or web page for the user to click on it and download a malicious file.
Pop-up messages telling that the user's machine is currently infected:
Pop-up messages posing as media player:
- Security Antivirus file to be downloaded:
- Security Tool file to be downloaded:
Friday, February 19, 2010
Porntube Anyone? Bonus Scareware!

Porn clips are everywhere! But then again, rogue antivirus software are everywhere too.
The fake video codec tactic targets unsuspecting users wanting to view the adult videos purportedly being hosted in the malicious website:
hxxp://porntube2000.com
Clicking on one of the thumbnails presents a video player window with the error message "Video ActiveX Object Error". The message asks the user install a new version of Video ActiveX Object which is actually an installer for Security Tool posing as a fake video codec.
This page also shows the following messageboxes when the user tries to move away from the malicious website and basically does not allow the user to select cancel.
Friday, January 22, 2010
Social Engineering Tactics Promote "Miracle" Berries
Af first I thought, wow this would be a good time to catch up.
She buzzed me and asked me if I was busy, then gave me a URL to try out very quickly and tell her what the results tell me.
Well, here's the screenshot:
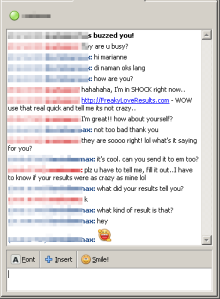
The link was:
hxxp://freakyloverresults.comAt this time I was already suspicious about the whole thing. So I tried out the link in a controlled environment. There were a series of redirections and my browser was redirected to:
hxxp://www.acaipowermax.com
It seems that whoever I was talking to was not my friend (possibly a bot). She might have been a victim of a phishing scam, and her Yahoo! IM account was being used as part of this social engineering tactic in order execute the Acai Berry spam which has been bugging people for ages.
This one was a bit harmless as the whole exercise was just another form of spam. But as always, I would like to remind everyone to be careful of clicking links, even if they come from people you know.