...public distribution of this Update through the official website »www.microsoft.com would have result in efficient creation of a malicious software, we made a decision to issue an experimental private version of an update for all users Microsoft Windows OS.
as the computer set to receive notifications when new updates are available, which you have received this notice.
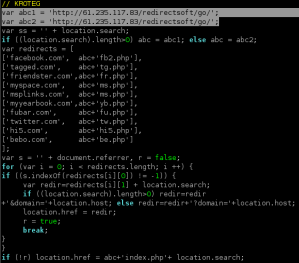
We have seen emails containing one of the following links:
hxxp://www2.sinel.com/microsoftupdate.html
hxxp://mail1.e-corecorporation.com/default.htmThey seem to be compromized websites being used by the bad guys in order to facilitate this attack.
The page default.html from
hxxp://mail1.e-corecorporation.com/default.htm uses a refresh-type redirect to this url:hxxp://0xc0.0xdc.0x6e.0xe4/microsoftupdate.htmlThe page microsoftupdate.html from
sinel.com and 0xc0.0xdc.0x6e.0xe4 both execute another refresh-type redirect in order to download a Zeus malware with filename update09.exe.Interestingly enough, this attack uses 0xc0.0xdc.0x6e.0xe4 to serve the malware. This IP-address translates to 192.220.110.228, which in turn resolves to summit102.summitdesign.net, another possibly compromised website used in this attack.
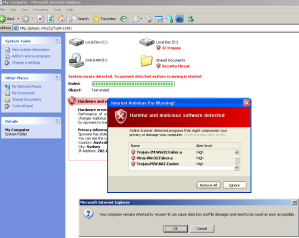
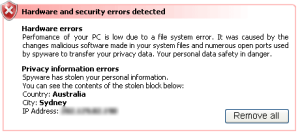
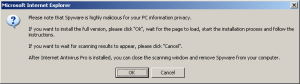
The presence of the following files/folders may indicate signs of infection:
%System%\sdra64.exe
%Temp%\tmp.exe
%System%\lowsec\More here.